Home / Solutions / SENTRYGuard Collaboration
Without knowing how exposed your business is, how can you possibly protect it.
Why? Cloud posture monitoring involves continuously assessing and managing the security of a business’s cloud environment. This includes tracking suspicious logins, ensuring users have multi-factor authentication (MFA) enabled, monitoring email forwarding rules, and identifying misconfigurations that could lead to security vulnerabilities.
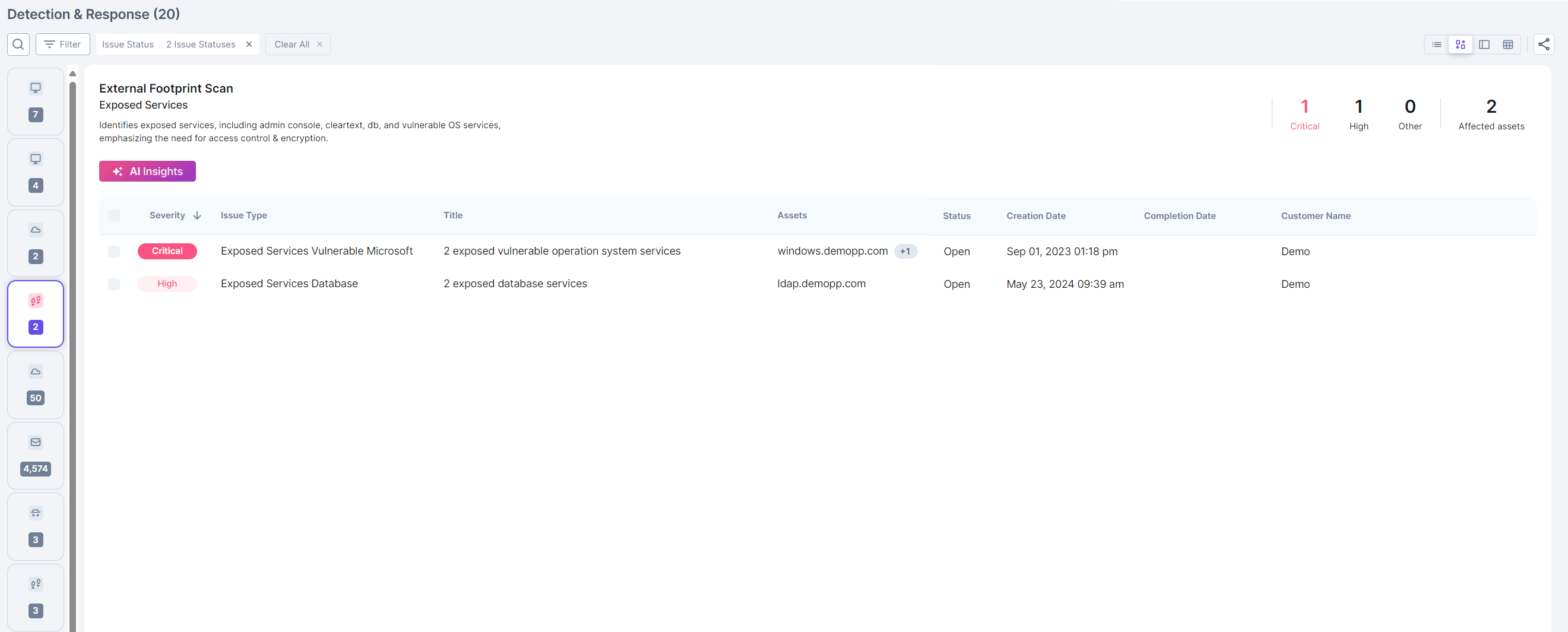
Why? External footprint scanning involves regularly assessing a business’s internet-facing assets to identify exposed services, expired SSL certificates, website vulnerabilities, and other security risks. This proactive approach helps SMBs understand and mitigate potential entry points for attackers.
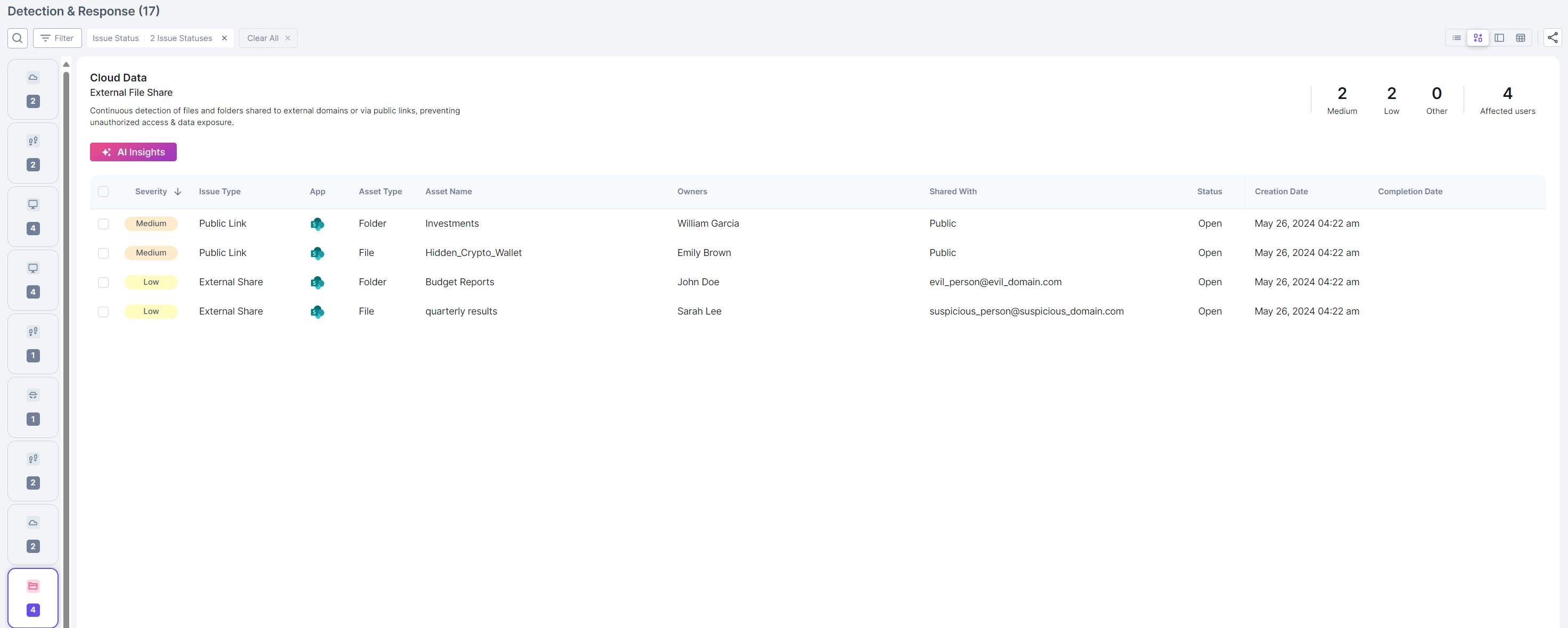
Why? Cloud data protection involves monitoring and securing your company’s data stored in the cloud to prevent unauthorized access or exposure. This includes detecting publicly accessible data, misconfigurations, and improper sharing that could lead to data breaches.
Why? Microsoft Defender for Office 365 provides a comprehensive suite of tools to protect your business’s email and collaboration environment from threats such as spam, malware, phishing, and data leaks. It combines advanced security features like email encryption, safe links, and real-time threat intelligence to ensure your communications remain secure.
In today’s interconnected digital landscape, securing your SMB’s cloud environment is more crucial than ever. Cloud directory posture monitoring ensures that suspicious logins, MFA status, and email forwarding are closely tracked, while external footprint scans identify exposed services, outdated SSL certificates, and website vulnerabilities that could be exploited by attackers. By proactively managing these areas, your business can prevent unauthorized access and mitigate potential threats before they escalate into major security incidents.
Effective cloud data protection is essential for safeguarding sensitive company information from being publicly exposed. Continuous monitoring, strict access controls, and encryption help keep your data secure in the cloud. Meanwhile, tools like Microsoft Defender for Office 365 provide comprehensive email protection, blocking phishing, malware, and spam, while securing communications with encryption and safe links. By integrating these layers of protection, your SMB can maintain a strong security posture across both cloud services and email communications, reducing the risk of breaches and data loss.